Investigate 10 of the most perilous malware dangers so you can rapidly and unequivocally distinguish, forestall, shield, and answer assaults. The vast majority of little to medium-sized organizations are in danger of malware-based interruptions or assaults. Also, assaults on huge corporate gatherings are turning out to be more risky and unsafe than any time in recent memory. Get guidance on many topics on TechKorr.
Sorts of malware and dangers from them
The term malware is a portmanteau of “malevolent” and “programming”. As you likely know, malware addresses a colossal network safety danger in all conditions and biological systems. Any piece of meddlesome and horrendous programming program – particularly those that compromise gadget capacities take information, spy on clients, and by and large reason tumult – is a sort of malware.
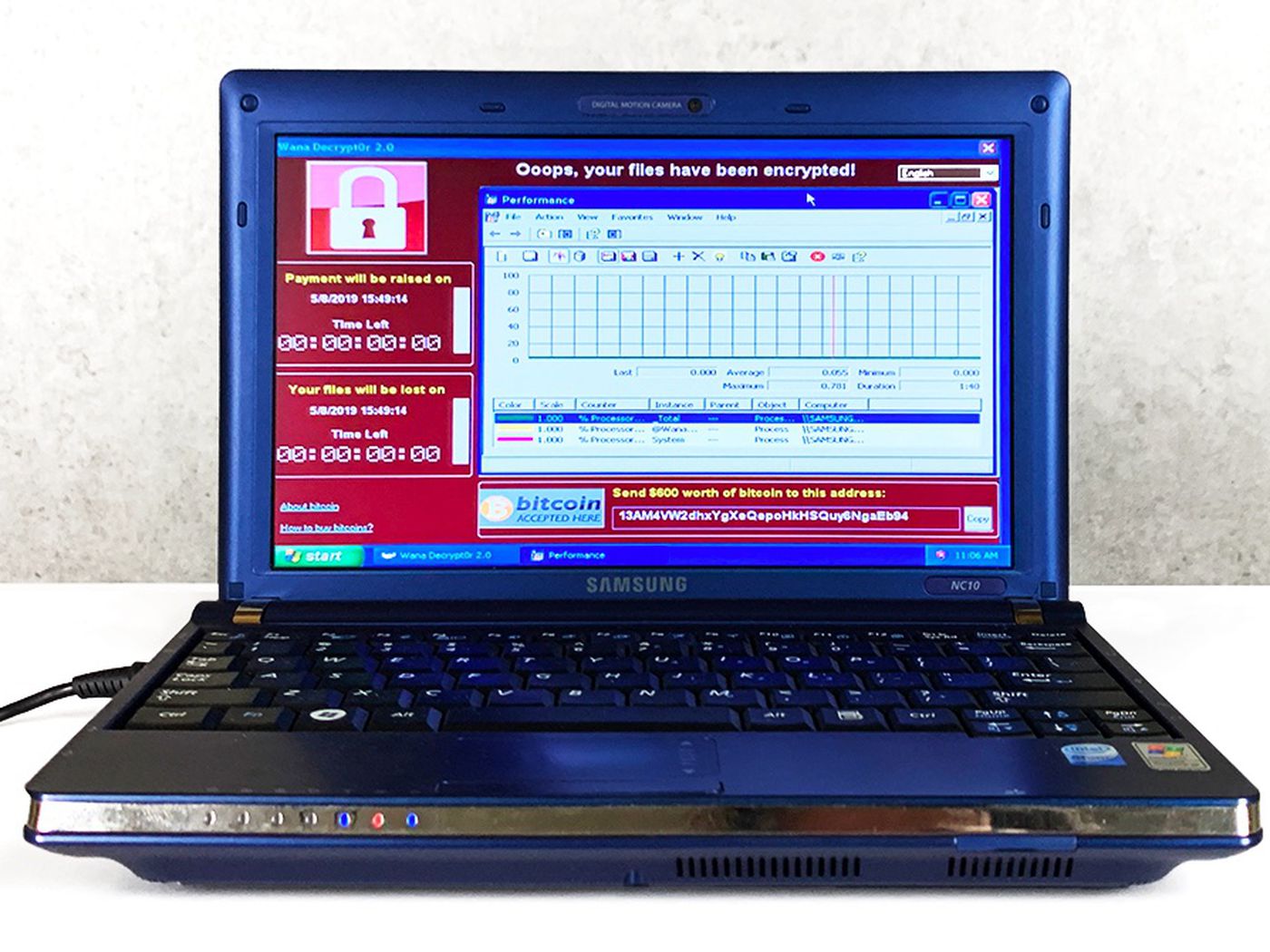
Klopp ransomware
Klopp is one of the latest and most perilous ransomware dangers to arise. It addresses a variation of the notorious Cryptomix ransomware, which normally hits Windows clients.
Before it begins scrambling, the Klopp ransomware blocks more than 600 Windows processes and handicaps numerous Windows 10 applications, including Windows Defender and Microsoft Security Essentials, seriously diminishing your possibilities of safeguarding information. Do you know about the VBS: Malware-gen?
Windows OS Ransomware
As of late, programmers have dispersed messages training focuses on quickly introducing Windows OS refreshes. Whenever clients begin downloading the necessary update, ransomware ‘.exe’ records advance toward the gadget. Email security controls and an extensive incorporated security arrangement can assist with forestalling these sorts of malware occurrences.
Zeus game over
This malware type is essential for the “Zeus” group of malware. Zeus Gameover is a Trojan – a malware masked as something genuine – whose design is to get monetary data, with which to take whatever is in a ledger.
Specialists say the most troublesome part of this malware is that it doesn’t need a unified “order and control” server to finish exchanges, making it more straightforward for agents and policing to recognize the culprits behind these hacks. becomes testing.
Slayer malware
This kind of malware influences macOS gadgets and depends on Flash updates and social designing strategies to fool casualties into introducing malware on the gadgets. At first, the programmers utilized a particular zero-day weakness to send off this danger. In any case, programmers are concocting new plans to bring this malware to PCs that generally depend on friendly designing strategies.
Specialist Tesla
Specialist Tesla is a strong, simple-to-utilize type of spyware. In particular, Agent Tesla is a Remote Access Trojan (RAT) that lets out qualifications, logs keystrokes, duplicates clipboard information, and gathers pictures from the casualty’s PC. Lately, malware has seen an immense leap in prominence, and in excess of 6,000 loathsome people pay a membership charge to permit the product.
Rasa
Ransomware-as-a-Service (RaaS) has acquired boundless prevalence among ransomware groups for various reasons. The development of Ras features how simple it is for non-coders and non-specialized individuals to complete ransomware assaults.
Fleeceware
Despite the fact that people might eliminate certain applications from their telephones, Fleasware keeps on charging application clients huge amounts of cash. As indicated by an ongoing exploration, north of 600 million Android clients have unconsciously downloaded “Fleeceware” on gadgets in the a couple of years.
While Fleeceware doesn’t address a significant security danger to protection or information, Fleeceware is still strikingly normal. It’s an ambiguous practice that application designers engage in.
IoT Device Attack
Have you as of late introduced a shrewd doorbell, or gotten savvy speakers? Programmers are attempting to take advantage of the weaknesses of these instruments to take data.
Programmers target IoT gadgets for an assortment of reasons. In many examples, IoT gadgets are so little (there is so little capacity) that they can’t oblige legitimate safety efforts. IoT gadgets ordinarily contain simple to-get to information, going from passwords to usernames. Programmers utilize this information to break into records and take more data.
Cryptojacking
Cryptojacking addresses a security danger that is totally one of a kind to digital forms of money. Crypto-malware successfully shields programmers from huge overheads, as it permits them to “mine” digital forms of money without paying for costly mining equipment or piling up enormous power bills. Whenever digital forms of money are mined, they are shipped off crypto-wallets that are constrained by malware administrators.